MailPassView is a popular tool designed to recover and display stored email account passwords from various email clients, such as Microsoft Outlook, Mozilla Thunderbird, and others. Developed by NirSoft, it allows users to easily retrieve forgotten or saved passwords and account details from their computers. While this tool can be incredibly useful, it also raises an important question: Is using MailPassView legal?
The legality of using MailPassView depends on how and where it is used. On one hand, it can be perfectly legal when used on your own devices to recover passwords for accounts that belong to you. On the other hand, using it on someone else’s device or to access accounts without permission may have serious legal implications.
We will explore the legal boundaries of using MailPassView, highlighting both the legitimate and potentially unlawful uses of the tool. We will also discuss ethical considerations and provide advice on using password recovery tools responsibly to avoid legal consequences.
What is MailPassView?
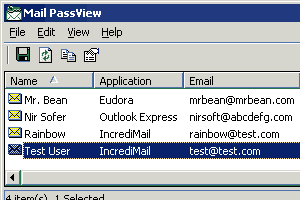
MailPassView is a free, portable password recovery tool developed by NirSoft. It is designed to help users recover lost or forgotten email account passwords that have been stored by email clients or applications.
Here’s a deeper look at MailPassView and its functionality:
Primary Function:
MailPassView scans your system for installed email clients and applications, then retrieves any stored email account information—such as usernames, passwords, and server settings (SMTP, IMAP, POP3). It makes it easier for users to recover credentials from their email applications without needing to remember or manually reset passwords.
Key Features:
Password Recovery: It recovers stored passwords for various email clients, including Microsoft Outlook, Windows Live Mail, Mozilla Thunderbird, and others.
Account Information: It displays important details like the username, password, and server information (e.g., POP3/SMTP settings).
Supports Popular Email Providers: MailPassView works with email clients configured to access Gmail, Yahoo Mail, Outlook, and other services via POP3 or IMAP.
Portable: The tool does not require installation, making it easy to run directly from a USB drive or any directory without altering your system.
Simple Interface: The program has an intuitive, easy-to-use interface that immediately displays recovered passwords once the scan is complete.
Export Options: Users can export the recovered data to a text file or copy it to the clipboard.
Supported Email Clients:
MailPassView works with several widely-used email applications, such as:
- Microsoft Outlook (including versions from Outlook 2000 to Outlook 2019)
- Windows Live Mail
- Mozilla Thunderbird
- Eudora
- The Bat!
- Gmail, Yahoo Mail, and other popular providers (when configured in the client via IMAP or POP3).
How It Works:
Scan: After launching MailPassView, the program scans your computer’s email client configurations.
Display: It identifies saved email accounts and displays account details, such as email addresses, usernames, passwords, and server information.
Recover: The tool allows users to recover passwords and view the associated settings directly on the interface.
Export: It enables exporting the recovered data into a text file for future reference or backup.
Security Considerations:
MailPassView is a powerful tool, but it should only be used responsibly. Since it can retrieve sensitive account information, it is crucial that it is only used on devices you own or have explicit permission to access.
MailPassView is a simple and efficient utility that helps users recover lost or forgotten passwords from their email clients. While it’s a useful tool for password recovery, it should be used with caution to ensure that it is employed legally and ethically.
Legal Use of MailPassView
MailPassView is a useful tool for recovering saved passwords from email clients and accounts on your computer. While it is powerful, it’s important to understand the legal boundaries within which it can be used. Here’s an explanation of what constitutes legal use of MailPassView:
1.Using MailPassView on Your Own Devices
Personal Devices: MailPassView is perfectly legal to use on systems you own, such as your personal computer or mobile device. If you’ve set up email accounts and stored passwords within email clients (like Outlook or Thunderbird), it’s completely lawful for you to use MailPassView to retrieve those credentials.
Forgotten Credentials: If you’ve forgotten the password to one of your email accounts but the account is yours (for example, you’ve lost the password to your Gmail account set up in Outlook), using MailPassView is a convenient and legal way to recover those passwords.
Email Accounts You Control: As long as you are the owner of the email account or you have permission to access the account, it’s perfectly legal to retrieve the credentials using MailPassView. This applies even to email accounts that you may have set up for business or other personal purposes.
2.Password Recovery for Forgotten Credentials
Password Recovery Tool: One of the main uses of MailPassView is to help users recover passwords they have forgotten. If you’ve set up an email account in a client (such as Outlook or Thunderbird) and can’t remember the password to access it, MailPassView can help you retrieve that password legally.
No Harm to Others: If the account is your own and you’ve just misplaced the password, using MailPassView ensures that no unauthorized access is involved. The tool simply pulls the password from your system’s stored credentials, and this is legal as long as it’s used on accounts you own.
3.Recovering Passwords for Accounts You Have Access To
Multiple Email Accounts: You may have multiple email accounts configured on your computer. If you’re the owner of these accounts, using MailPassView to recover lost or forgotten credentials is legal, as long as you are accessing your own accounts.
Reclaiming Lost Access: If you’ve been locked out of an email account or lost access for any reason, MailPassView can provide a quick recovery method to reclaim access to the accounts you control, helping to ensure you can access important emails.
4.Using MailPassView in an Organizational Setting (With Permission)
Corporate Use (with Permission): In a business environment, an IT administrator or system administrator could use MailPassView (with proper permission) to recover email account passwords for company accounts. This may be necessary for troubleshooting or in situations where employees forget their passwords, and access needs to be restored.
Authorized Access: If the organization owns the devices or the accounts, and the user is authorized to access those accounts, using MailPassView could be a legal and efficient way to recover information.
5.Recovering Access to Backup Email Accounts
Backup or Secondary Accounts: Many people set up secondary or backup email accounts for account recovery purposes. If you’re trying to recover access to one of these accounts, using MailPassView on your own system (where the account is configured) to retrieve the password is entirely legal.
Summary of Legal Use
- On your own devices: Legal to use MailPassView on computers you own, to recover passwords for email accounts you control.
- Personal recovery: If you’ve forgotten your email passwords or lost access, using MailPassView to retrieve credentials from your own email client is completely legal.
- With explicit permission: Using it on devices or accounts you’ve been authorized to access (such as for organizational recovery, under permission) is also legal.
As long as you are accessing only your own accounts or have the proper permissions, using MailPassView falls within legal boundaries and can serve as a helpful tool for managing forgotten credentials.
Unauthorized Use and Potential Legal Risks
MailPassView is a powerful tool for recovering email account passwords, but like any tool that deals with sensitive information, it carries significant legal and ethical implications. Unauthorized use of MailPassView—using it on a device or account you don’t own or have permission to access—can lead to serious legal consequences.
Here’s a breakdown of the potential legal risks associated with using MailPassView without authorization:
1.Using MailPassView on Someone Else’s Device
Definition of Unauthorized Use:Using MailPassView to recover passwords from a device that doesn’t belong to you, without the owner’s knowledge or consent, is considered unauthorized access.
Legal Consequences:
In many jurisdictions, unauthorized access to someone else’s electronic devices, accounts, or data is illegal.
Depending on the country or region, this can be classified as computer fraud, hacking, or invasion of privacy.
Legal penalties could include fines, civil lawsuits, or even criminal charges, depending on the severity of the breach and the local laws.
Examples of Unauthorized Use:
Using MailPassView on a coworker’s computer without permission to access their email account.
Trying to recover passwords from a family member’s email without their knowledge or consent.
2.Violating Privacy Laws
Data Privacy and Protection Laws:
Many countries have strict laws governing the protection of personal information and privacy.
For example:
General Data Protection Regulation (GDPR) in the European Union protects personal data and ensures individuals have control over their data.
Computer Fraud and Abuse Act (CFAA) in the U.S. criminalizes unauthorized access to computers and accounts.
Risks of Violating Privacy Laws:
If you use MailPassView to recover passwords from someone else’s account without their permission, you could be violating privacy laws.
Legal consequences can include hefty fines or imprisonment, especially if sensitive information is accessed or used maliciously.
Breach of Trust:
Even if the device or account doesn’t contain sensitive data, unauthorized access can still lead to a breach of trust. Victims of unauthorized access might take legal action against the individual who accessed their accounts.
3.Hacking and Cybercrime
Definition of Hacking:
In a legal context, hacking typically refers to the unauthorized use or exploitation of a computer system or network to access data. Using MailPassView to retrieve passwords from an account you don’t own without consent can be seen as a form of hacking.
Penalties for Hacking:
Criminal Charges: Many countries classify unauthorized access as cybercrime and impose criminal penalties for hacking.
Fines and Jail Time: Convictions for hacking can result in significant fines, and in some cases, jail sentences.
Malicious Intent:
Even if the use of MailPassView is not intended to harm someone, accessing accounts without permission can still be seen as malicious activity under the law. It’s important to recognize that the intent behind the action doesn’t always matter when it comes to legal matters involving privacy and unauthorized access.
4.Civil Lawsuits
Potential for Lawsuits:
If someone uses MailPassView to access your email or online accounts without permission, you have the right to take legal action. Victims of unauthorized access can file civil lawsuits seeking damages for any harm caused.
Types of Damages:
Civil lawsuits could seek compensation for:
- Emotional distress due to the invasion of privacy.
- Financial losses if sensitive information was exploited.
- Punitive damages if the court finds the action was particularly malicious.
5.Risks in Business or Employment Context
Employers and Employees:
Employers typically have systems in place to monitor company-issued devices and accounts. If an employee uses MailPassView to recover passwords from other employees’ accounts or company emails without permission, they could face disciplinary action, termination, and legal consequences.
Corporate Espionage:
In some cases, unauthorized use of password recovery tools can lead to corporate espionage, where sensitive business data is accessed or stolen. This is a serious offense, and individuals involved in corporate espionage can face significant criminal penalties.
Ethical Considerations
Ethical considerations are essential when using any tool that has the ability to recover passwords or access private information, such as MailPassView. While the tool itself is not inherently malicious, its use can raise significant ethical concerns depending on the context. Here’s an exploration of the key ethical considerations when using MailPassView:
1.Respecting Others’ Privacy
Personal Data Privacy: One of the most crucial ethical concerns when using MailPassView is respecting the privacy of others. Passwords and account details are sensitive information, and accessing someone else’s email account without their consent is an infringement on their privacy. This is especially true if you’re using MailPassView to recover or view passwords for accounts that belong to others.
Confidentiality: Many emails contain private, personal, or confidential information. Even if the intent is not malicious, accessing this data without authorization is an ethical violation. Respecting someone’s digital footprint, just as you would their physical space, is fundamental in maintaining ethical standards.
2.Personal Accountability
Acting with Integrity: When using MailPassView, it’s essential to use the tool for ethical and legitimate reasons. You should only recover passwords or account details for accounts you own or have explicit permission to access. For example, if you’re helping a friend recover their account, ensure they are fully aware of the actions you’re taking, and that they approve it.
Understanding Consequences: The ethical use of MailPassView also involves being aware of the potential consequences of improper use. Using the tool to access private information without consent may not only be illegal but can also harm relationships, breach trust, and cause emotional distress to the person whose data has been compromised.
3.Preventing Harm
Avoiding Exploitation: Tools like MailPassView can be exploited if used maliciously, either by accessing sensitive information for personal gain or by causing harm to individuals or organizations. Ethical use includes considering the potential risks, such as identity theft or fraud, that could arise from recovering someone else’s password or personal information.
Handling Recovered Data Safely: If you’re recovering your own passwords or assisting others with recovery, it’s important to ensure that the recovered data is treated securely. For instance, passwords should not be shared carelessly, and any sensitive information should be stored or discarded securely to prevent it from falling into the wrong hands.
4.Legal and Ethical Boundaries
Legality Equals Ethics: While some actions may be technically legal, they may still be ethically questionable. For example, just because MailPassView can be legally downloaded and used doesn’t mean it should be used to access others’ accounts without permission. Ethically, individuals must stay within legal boundaries to ensure their actions align with both the letter and spirit of the law.
Informed Consent: Always ensure that the person whose account is being accessed (even if you are helping them) is fully informed and has provided consent. Informed consent means they understand what you are doing, why you are doing it, and any potential risks involved.
5.Safeguarding Trust
Maintaining Trustworthiness: Ethical use of MailPassView is also about safeguarding the trust of those around you, particularly if you’re using the tool for personal or professional purposes. If someone has given you access to their system to recover passwords, ensuring you don’t misuse this trust is key. Misusing access or violating that trust can have long-lasting ethical and reputational consequences.
Transparency and Communication: Being transparent about your intentions when using MailPassView is a crucial part of ethical behavior. If you’re recovering passwords for someone, it’s important to communicate what actions you’re taking and why. This ensures that the person is fully aware and can make informed decisions.
Alternatives for Legal and Safe Password Recovery
If you’re looking to recover lost passwords but want to ensure that the process is secure, ethical, and legal, there are several alternatives to using tools like MailPassView. Below are some safe and legal methods you can consider:
1.Password Managers
What They Are: Password managers are software tools designed to store and manage your passwords securely. They encrypt your passwords, making it easy to store and retrieve them without having to remember each one.
Why They Are Safe and Legal:
Encryption: Password managers use strong encryption to protect your data, ensuring that only you have access to your passwords.
Legitimate Use: They are designed to help users securely manage passwords and recover them when needed.
Multi-Device Syncing: They typically allow synchronization across multiple devices, making password recovery easier and more secure.
- Popular Password Managers:
1Password: A widely trusted password manager known for its strong encryption and ease of use.
LastPass: Offers both free and premium versions with encrypted storage and password recovery options.
Dashlane: Another strong option with built-in password recovery features and dark web monitoring.
- How They Help:
When you forget a password, most password managers offer recovery options, including the ability to reset the master password using a recovery key or secondary authentication methods.
2.Built-in Account Recovery Options
What They Are: Most email and online accounts come with their own recovery features, such as password reset links, security questions, or two-factor authentication (2FA) to help recover a lost password.
- Why They Are Safe and Legal:
Official Channels: These methods are provided directly by the service providers, ensuring that you’re following the legal procedures set by the provider.
No Third-party Tools Needed: You don’t need to use third-party software, making it the most secure and straightforward option.
- How They Help:
Email Account Recovery (e.g., Gmail, Outlook): If you forget your password, you can use the “Forgot Password” option to reset your email password using a secondary email, phone number, or 2FA code.
Security Questions: For accounts without 2FA, answering pre-set security questions can help you regain access.
Two-Factor Authentication (2FA): If you set up 2FA, most services offer backup codes or alternate ways to verify your identity.
- How to Use:
Simply navigate to the password recovery page of your email provider or service.
Follow the steps, such as receiving a reset link via your backup email or SMS.
3.Official Password Recovery Tools
Many software and online services offer official tools to recover passwords or reset them in a secure manner. These tools typically involve a secure password reset process.
Why They Are Safe and Legal:
Designed by Service Providers: These tools are offered by the service providers themselves, ensuring they follow industry standards for security and privacy.
Compliance with Regulations: Providers comply with data protection regulations such as GDPR and CCPA, offering secure and legal methods to recover passwords.
How They Help:
Windows Password Recovery Tool: If you forget your Windows login password, Microsoft offers tools to reset or recover your password through a Microsoft account if linked.
Apple iCloud Password Recovery: Apple offers a recovery process through iCloud or your Apple ID for Apple devices.
Online Banking or Social Media Recovery: Banks and social media platforms have secure password recovery processes, typically involving verification through email, SMS, or identity verification.
- How to Use:
Visit the official recovery or support page for your device or service (e.g., Apple, Microsoft, Google).
Follow the guided steps to verify your identity and recover your password.
4.Biometric Authentication
What It Is: Biometric authentication includes using your fingerprints, face recognition, or voice recognition to unlock your device or accounts, making password recovery more seamless and secure.
- Why It Is Safe and Legal:
Built-in Security: Most modern devices and services offer biometric authentication as a secure and legal alternative to traditional password entry.
Protection of Personal Data: Biometric data is securely stored on the device (not online), reducing the risk of data breaches.
- How It Helps:
Biometric authentication allows you to bypass the need for passwords entirely, making it a simple solution for secure device access.
In case you forget your password, biometrics can be used to reset or recover the access code for your device.
- How to Use:
Enable biometric authentication (fingerprint, face recognition) in the settings of your device or service.
When logging in, the system will use your biometric data for authentication.
5.Account Recovery Services by Third-Party Providers
What They Are: Some professional password recovery services offer legal methods to help recover lost or forgotten credentials. These services can recover passwords from encrypted files, databases, or email accounts.
Why They Are Safe and Legal:
Authorization Required: Legal recovery services require your authorization to help recover passwords, ensuring you’re the rightful owner of the account.
Compliance with Regulations: These services operate under the regulations of the data protection laws, so they respect privacy and security.
- How They Help:
These services may use brute-force or dictionary attacks to recover encrypted passwords.
They can assist in recovering access to locked files, email accounts, or databases.
- How to Use:
Contact a reputable password recovery service provider.
Provide required details to verify your ownership of the account or files you wish to recover.
conclusion
MailPassView is legal when recovering passwords for accounts you own or have permission to access. It serves as a legitimate tool for personal password recovery. However, using it on someone else’s device or to access accounts without consent is illegal and violates privacy laws. Ethical considerations should guide its use, emphasizing respect for others’ privacy. Always ensure you have authorization before using such tools to avoid legal repercussions. For secure alternatives, consider official recovery methods or password managers.